


August 2023 | Nextworks
You are likely rather familiar with multi-factor authentication (MFA / 2FA) by now. Logging into the myriad of the online services you use daily can trigger a text message to your phone or require a code from an Authenticator App. This additional security step is an effective mechanism to help protect your identity, finances, and data.
MFA allows you to prove that it is indeed you, and not a cybercriminal, who is trying to access your bank account, health records, etc. We highly suggest enabling MFA whenever possible. You can usually enable MFA in your account settings. While MFA does pose some inconvenience, it’s a prudent safeguard.
It would be nice to end here on this note: Cybercriminals are everywhere. Setup MFA on all your accounts. Sleep well at night.
Unfortunately, it’s no longer that simple. Cybercriminals now have several tricks to work around many MFA safeguards. Let’s explore one of their tricks: Adversary-in-The-Middle (AiTM) Phishing.
AiTM is not new. It’s been around for a few years. However, as more people activate MFA on their accounts, conventional Phishing is less successful. So AiTM Phishing attacks are becoming more common. Microsoft reports that since September 2021, MiFA Phishing has targeted more than 10,000 organizations.
As the name suggests, an AiTM attack places an agent in between you and the online service you are logging into. This agent shares information between the two parties and thus can hijack access to your account.
The below image explains the AiTM phishing process. (credits: Microsoft)
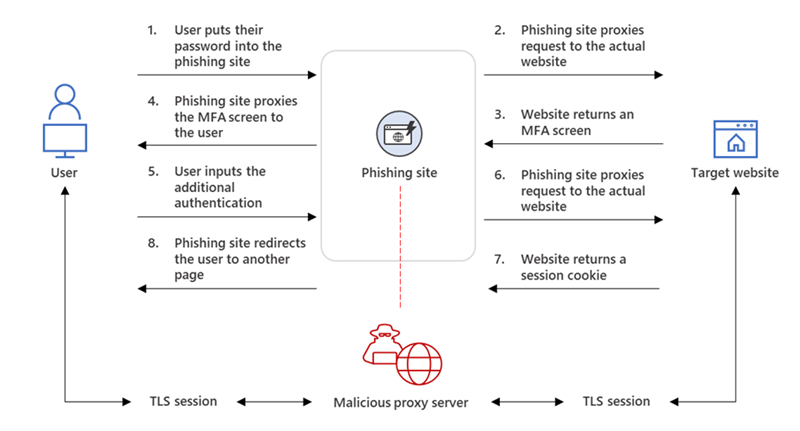
This process can also be explained using the following example.
You receive an email from your bank claiming that a $8,900 draft has triggered a security alert on your account. The email contains a link to log into your account to review the transaction.
The email appears to be legitimate. It’s clear, has your bank logo, and contains a recognizable link with "usbank.com" in the address. Concerned about the $8,900 transaction, you click the link.
(While the link text in the email shows "usbank.com", you didn’t notice that when you mouse over the link, the actual text of the link is "us-ebank-com.gt", and not "usbank.com".)
You now arrive at a counterfeit web site that appears to be the US Bank login page. You don’t notice the unusual "us-ebank-com.gt" address at the top of your browser. You are too busy thinking, “What is this $8,900 charge for?” You promptly enter your username and password to get to the bottom of it.
The web site you are now on is in fact driven by the AiTM software. And now, you have provided the hacker with your online banking credentials. Okay, no big deal, right? You have MFA enabled and they can’t get into your bank account without the code. Well, perhaps they can.
After entering your username and password into the AiTM web site, the hacker then passes those credentials to the actual US Bank web site. US Bank detects that a new, untrusted device is attempting to log in. So, US Bank texts a login notice with a code to your smartphone.
Anticipating this, the AiTM web site now asks you for that code. You type in the code, still thinking you are at the US Bank login page. The hacker then provides that code to the real US Bank web site. And now they are in your account.
Meanwhile, you are presented with a fake US Bank notice that reads “We apologize, but US Bank e-banking is down for maintenance. Please try again later.” You don’t know that your bank account has been compromised, at least for now. This give the hacker the time they need while you wait to try again later.
And that’s how an AiTM Phishing scam works.
First and foremost is to get cybersecurity training for you and your staff. Here are a few tips:
Conventional MFA is still far better than no MFA at all. Conventional Phishing is far more common than AiTM Phishing. If conventional MFA (text messaging) is your only option, then you should still enable it.
Cybersecurity is a tiered approach. Numerous basic precautions can amount to a lot of protection. But without professional IT help, cyber-safety can be difficult to achieve.

Contact Nextworks today for a no cost Cybersecurity Assessment.
Or, learn more about Nextworks IT Services.